The Windows firewall blocks unsolicited incoming traffic, and this behavior means that individual programs do not have to be defined in the firewall exceptions list in order for those programs to function behind the Windows firewall. The Windows STIGs includes some firewall rules for Core Networking components, but additional rules may occasionally be required at a local site. Firewall rules that are defined in separate group policy objects are cumulative.
The purpose of this documentation is to explain the process of creating a firewall customization group policy object.
This steps below assume that a Group Policy Object has been named, checked out, and is open for editing. In this example, the GPO TacomaWA-W Firewall Customization – Ultrabac is being edited. The rule will allow inbound connections for TCP 1910.
Consider using an apropriate filter, such as the Windows 10 WMI filter, to ensure the Firewall Customization will only apply to appropriate Windows systems. This can be done by requesting a new GPO with the WMI filter in place, or by requesting that the WMI filter is added when the GPO is deployed. For more information on AGPM, see: http://tst.usgs.gov/applications/security/advanced-group-policy-management/
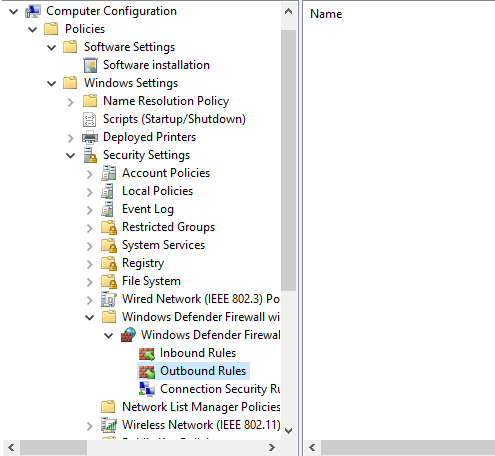
Expand Computer Configuration\Policies\Windows Settings\Security Settings\Windows Defender Firewall with Advanced Security. Expand the next node that begins with Windows Defender Firewall with Advanced Security.., right-click on Inbound Rules, and click New Rule… to start the New Inbound Rule Wizard

Select the type of Rule. In this example, Port is selected. Click .

Define the Protocol and Ports for the rule. In this example, TCP is chosen and the port 1910 is specified. Click .

Define the action to be taken with this rule. In this example, Allow the connection is selected. .

Check all of the profiles to which the firewall rule will apply. In this example, Ultrabac traffic will only be allowed when the system is on connected to the GS Domain and the Domain firewall profile is in use. Click .

Give the rule a name and a desciption. Click .

The Rule is now listed in the right-hand pane. To make additional, or more granular adjustments, double click on the Rule.

The firewall rule can be further defined for specific programs, computers, or users. In this example, no additional configuration was made.
Follow the standard procedures for checking in and deploying the Group Policy Object. In the Group Policy Management Console, navigate to the appropriate OU, right click, and choose Link and Existing GPO.

In the select GPO window, scroll down to the GPO, highlight, and click . In this example, the TacomaWA-W Firewall Customization – Ultrabac GPO is selected.