Generic Security Service Application Program Interface (GSSAPI) allows for passthrough authentication using Active Directory Kerberos Tickets. The protocol is supported on all operating systems including Windows, Mac, Linux, and Solaris. This allows for passwordless authentication. When used alongside MIT Kerberos, you can also have Kerberos tickets sent for passwordless AD authentication on the host server.
Known Issues:
Sudo will not work unless setup for passwordless sudoers/wheel.
Required Software:
Install MIT Kerberos 3.2.2 via MCM
Optional: Install PuTTYCAC via MCM
Optional: Install MobaXTerm (Purchase of a license is required.)
GSSAPI Server Configuration:
You must configure the server that you wish to SSH into in advance with this configuration:
Red Hat Enterprise Linux (RHEL) 8.x, 9.x, and variants:
Edit /etc/ssh/sshd_config with the following lines and ensure you do not have duplicates:
GSSAPIAuthentication yes
GSSAPICleanupCredentials yes
GSSAPIStrictAcceptorCheck no
Ubuntu 22.04 (requires further testing):
Edit /etc/ssh/sshd_config with the following lines and ensure you do not have duplicates:
GSSAPIAuthentication yes
GSSAPICleanupCredentials yes
GSSAPIStrictAcceptorCheck no
GSSAPI Client Configuration:
Windows PowerShell OpenSSH
Use -K flag to pass credentials to the server. Please note the case sensitivity of the “K.” The use of uppercase “K” enables GSSAPI-based authentication and forwarding (delegation) while the use of lowercase “k” disables this!
ssh -K [servername.gs.doi.net]
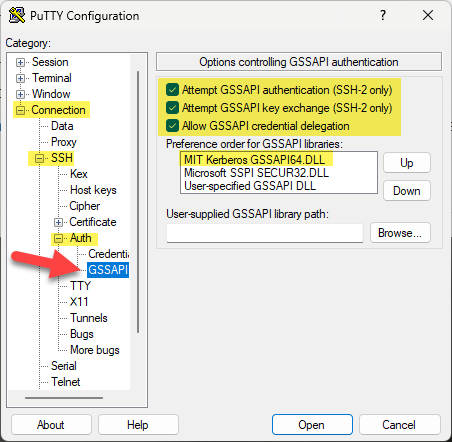
PuTTYCAC
With PuTTYCAC Open, Click on Connection, SSH, and expand Auth to get to GSSAPI. Make sure the 3 checkboxes are checked, and if needed MIT Kerberos GSSAPI64.DLL to the top order:
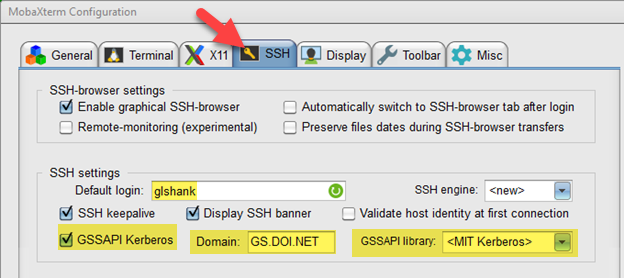
MobaXTerm
Click Settings, configuration, then the SSH tab. Click on GSSAPI Kerberos and set Domain to GS.DOI.NET. set default login to your samaccountname/shortname.