Apple Kerberos Single Single On (SSO) is a Configuration Profile applied to Jamf enrolled Macs for the purposes of Kerberos Ticket Granting Tokens (TGTs) used to authenticate the user to on-premise Active Directory resources. The user must be on VPN/on the DOI Network to get a Kerberos Ticket. When the user is on the network and a ticket needs to be refreshed or issued, a popup from macOS to “Sign into GS.DOI.NET” will be presented to the user. The ticket that is issued generally will last a day and is auto renewed as long as the machine is still on the network and the ticket is nearing expiration.
What’s the difference between Apple Kerberos SSO and AzureAD SSO?
| Apple Kerberos SSO (What this page is about) | Azure AD SSO (Link to page here.) |
| Uses the Kerberos SSO App Extension Type via Apple | Uses the Microsoft AzureAD SSO App Extension via Intune Company Portal.app |
| Supports apps that require Kerberos Tickets integrated with on-Premise Active Directory (SAMBA, DFS, etc) | Supports Microsoft 365, Apps, Websites, or services integrated with Azure AD |
Using Apple Kerberos Single Sign On (SSO)
1. Ensure that the Apple Kerberos Single Sign On Extension is available. You can check under System Settings, and type in “Profiles.” Look for something called “Kerberos SSO Extension.”
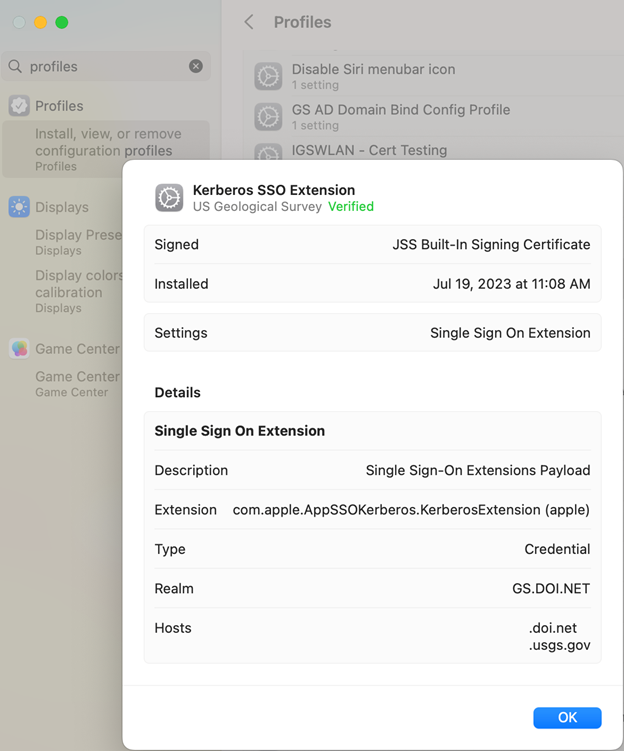
2. There will be a key icon on the menu bar when the SSO extension is available. When the key is not a ghost, a token has been issued. When the key is grayed out, a token has not been issued and is ready to be issued. Also, a user may receive a prompt to “Sign into GS.DOI.NET.”
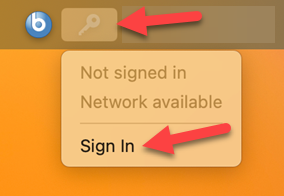
3. Click on Sign In from the Menu Bar (if the dialog box doesn’t appear).
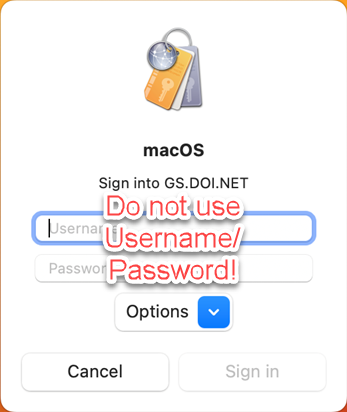
4. Ensure that the Smartcard and Smartcard Reader are plugged into the Mac, and under Options click on “Use a Smartcard or Identity.”
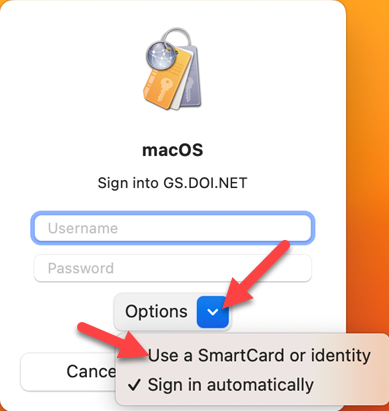
5. Under “Available Certificates” select your Certificate and click Select.
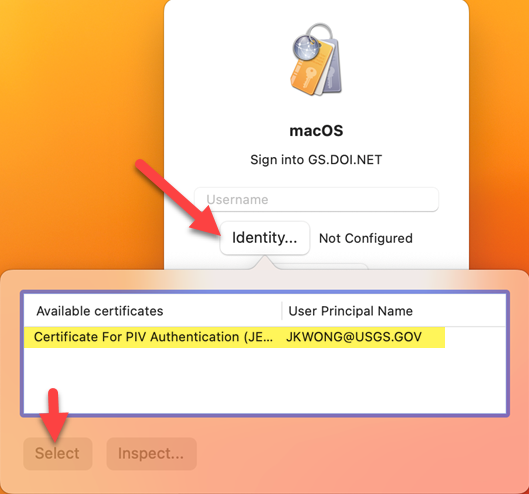
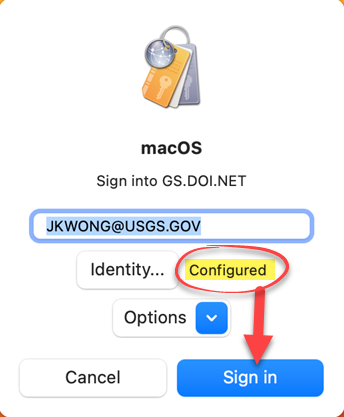
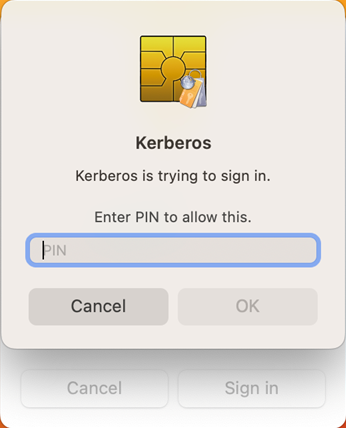
6. Click on Sign In, and you will be presented with “Kerberos is trying to sign in. Enter PIN to allow this.” Enter PIN.
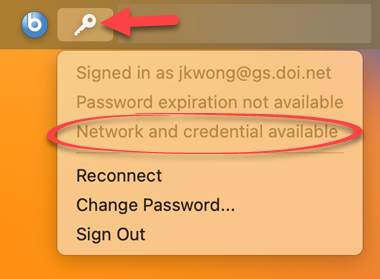
7. The key icon should not be ghosty, and clicking on it you should see that you are signed in, and Network and Credential are available.
Verify Kerberos Ticket has been issued
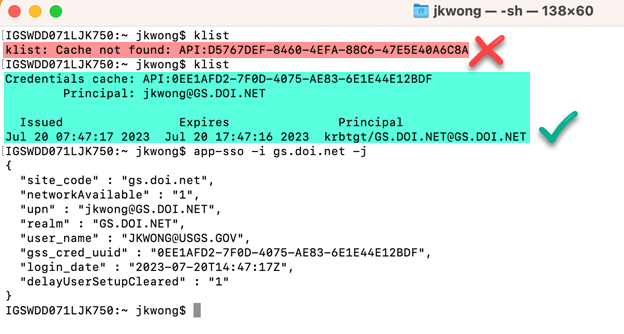
To verify if a ticket has been issued, open Terminal, and enter the command klist
If klist returns as “klist: Cache not found:” a Kerberos TGT has not been issued. If klist returns a Credentials Cache, you may inspect the details of the current Kerberos TGT issued as well as its expiration. For in-depth information, you may use the command app-sso -i gs.doi.net -j
Known Issues
I am unable to access my SMB/DFS shares via IP. Authentication will only work against a share resolve name that ends in gs.doi.net. This is to prevent unknown shares from gaining a Kerberos token. Try using the DFS Fully Qualified Domain Name Path (SMB://GS.DOI.NET/ShareName/etc).