Warning: Undefined variable $comment_tag in /afs/usgs.gov/www/tst/htdocs/wp-content/plugins/last-updated-shortcode/last-updated-shortcode.php on line 59
Last updated: September 20, 2021 at 17:53 pm PDT
An important component of information security is the destruction of data and media when they become obsolete, excess, or otherwise unnecessary. In order to comply with Federal, DOI, and USGS security mandates, each appropriate system administrator (SA) or system security manager (SSM) is required to ensure that data are properly handled throughout its lifecycle. The following guidance is intended to aid with the end of the data lifecycle – destruction of data – in compliance with established government security citations. However, the ultimate decision on how best to meet these security requirements is the responsibility of the local SA and SSM.
Types of Sanitization
NIST 800-88 Revision 1 specifies the following types of media sanitization
Clear
Clearing applies logical techniques to sanitize data in all user-addressable storage locations and protects against simple noninvasive data recovery techniques. Generally, it is applied through the standard Read and
Write commands to a storage device. For example, the software could overwrite the disk blocks with new values or providing a method to reset the device to the factory state (where rewriting is not supported).
Purge
Purging applies physical or logical techniques that render target data recovery infeasible using state-of-the-art laboratory techniques.
Destroy
Destroying renders target data recovery (using state-of-the-art laboratory techniques) infeasible and results in the media to no longer be able to store or retrieve data.
When deciding on how to sanitize media, SAs or SSMs should categorize the information to be protected, assess the nature of the medium
on which it is recorded, assess the risk to confidentiality, and determine the future plans for the media. Then choose the appropriate type(s) of sanitization. The chart below provides a decision process flow
to assist organizations in making sanitization decisions that are appropriate to the security categorization of the confidentiality of information contained on their media. This decision process is based on the confidentiality of the information, not the type of media. After the type of sanitization is determined for the information of the media, then the media type will guide the technique used to sanitize it.
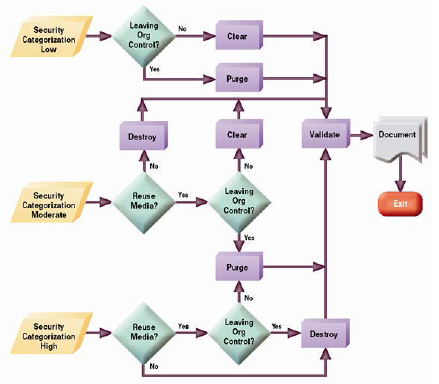
Examples and Guidance for Clearing, Purging, and Destroying Data
Media Sanitization Requirements
The type of sanitization performed depends on two factors:
- Whether or not the media is to be reused by the agency for continued use.
- Whether or not the media will be leaving agency control.
If the media will be reused by the agency, existing information on the media has a security classification of low, and will not be leaving organization control; then clearing is a sufficient method of sanitization. If the media will be reused and repurposed, has information w/ a security classification higher than low, and/or will be leaving organization control, (i.e., media being exchanged for warranty, cost rebate, or other purposes and where the specific media will not be returned to the agency), then purging should be selected as the sanitization method. If the media will not be reused at all, then destroying is the method for media sanitization.
| Media is going to be reused and has a security classification of low | Media to be reused w/ a security classification of moderate | Media is not to be reused | |
|---|---|---|---|
| Not leaving organizational control | Clear | Purge | Destroy |
| Leaving organizational control | Purge | Purge | Destroy |
Note – For some media, clearing media would not suffice for purging. However, for ATA disk drives manufactured after 2001 (over 15 GB) the terms clearing and purging have converged.
Recommendations for Clearing or Purging
The only way to guarantee all data has been erased from a hard drive is to overwrite all sectors on the disk with artificial information, such as overwriting configurations with random patterns of ones and zeros or to physically alter the drive by degaussing or mechanical destruction.
Specialized software applications allow for individual files, folders or entire drives to be “sanitized”, and made ready for re-utilization, donation or disposal. The specialized disk sanitizing software interacts directly with the drive and overwrites the selected files or the entire contents on the disk, including the boot record, master file tables, deleted files and contents of all files.
Software Recommendations
A simple way to sanitize a working disk that is not installed in your computer is to purchase a hard drive docking station. Then you can use software such as PartedMagic or CCleaner to wipe the drive (both support purging SSD media):
Many other free software applications are available to sanitize hard disks with lots of different options.
The technique for clearing, purging, and destroying media depends on the type of media being sanitized. The most common types of media are listed below with the recommended sanitization technique(s). Additional guidance on other types of media not specifically listed can be found in NIST SP 800-88, Guidelines for Media Sanitization.
| Media Type | Clear | Purge | Destroy |
|---|---|---|---|
| Magnetic Disks | |||
| Floppy Disks | Overwrite media by using agency approved software and validate the overwritten data. | Degauss in an NSA/CSS-approved degausser. | Incinerate floppy disks and diskettes by burning the floppy disks and diskettes in a licensed incinerator. Shred |
| ATA Hard Drives | Overwrite media by using agency-approved and validated overwriting technologies/ methods/tools. | Secure Erase,Degauss, or Disassemble and degauss the enclosed platters. | Incinerate hard disk drives by burning the hard disk drives in a licensed incinerator. Shred Pulverize Disintegrate |
| Zip Drives | Overwrite media by using agency-approved and validated overwriting technologies/ methods/tools. | Degauss using an NSA/CSS approved degausser. | Incinerate disks and diskettes by burning the zip disks in a licensed incinerator. Shred |
| SCSI Drives | Overwrite media by using agency-approved and validated overwriting technologies/ methods/tools. | Secure Erase, Degauss using an NSA/CSS approved degausser, or Disassemble and degauss the enclosed platters using an NSA/CSS approved degausser. | Incinerate hard disk drives by burning the hard disk drives in a licensed incinerator. Shred Pulverize Disintegrate |
| Magnetic Tape | |||
| Reel and Cassette | Overwriting should be performed on a system similar to the one that originally recorded the data. For example, overwrite previously recorded classified or sensitive VHS format video signals on a comparable VHS format recorder. All portions of the magnetic tape should be overwritten one time with known non-sensitive signals. | Degauss using an NSA/CSS approved degausser. | Incinerate by burning the tapes in a licensed incinerator. Shred |
| Optical Disks | |||
| CD/DVDs | N/A. See Destroy Method column. | N/A. See Destroy method column. | Destroy in order of recommendations: Removing the information bearing layers of DVD media using a commercial optical disk grinding device. Incinerate optical disk media (reduce to ash) using a licensed facility. Use optical disk media shredders or disintegrator devices to reduce to particles that have a nominal edge dimensions of five millimeters (5 mm) and surface area of twenty-five square millimeters 25 mm2). **** This is a current acceptable particle size. Any future disk media shredders obtained should reduce CD/DVD to surface area of .25mm. |
| Flash Media | |||
| USB Removable Drives | Overwrite media by using agency-approved and validated overwriting technologies/ methods/tools. | N/A. See Destroy method column. | Incinerate hard disk drives by burning the hard disk drives in a licensed incinerator. Shred Pulverize Disintegrate |
| Memory Cards | Overwrite media by using agency-approved and validated overwriting technologies/ methods/tools. | N/A. See Destroy method column. | Incinerate hard disk drives by burning the hard disk drives in a licensed incinerator. Shred Pulverize Disintegrate |
| Solid State Drives | Overwrite media by using agency-approved and validated overwriting technologies/ methods/tools. | Secure Erase of Crytographic Erase * | Incinerate hard disk drives by burning the hard disk drives in a licensed incinerator. Shred Pulverize Disintegrate |
* Note: Degaussing is not an appropriate method of purging data from flash media.
Hard Copy Media
Information contained in hard copy material.
Burning
The material must be burned in an incinerator that produces enough heat to burn the entire bundle, or the bundle must be separated to ensure that all pages are incinerated.
Shredding
NIST requires 1mm x 5mm cross cut shred size from our previous 5/16” shred size requirement. This requirement is taken directly from NIST SP800-88 and applies to the moderate classification for FTI. Safeguards is aware that this change in shred size is a requirement that may take agencies time to adjust to,
either by purchasing compliant shredders, or requiring a revision to an existing contract.
Destroy paper using cross cut shredders which produce particles that are 1 mm x 5mm (0.04 in. x 0.2 in.) in size (or smaller), or pulverize/disintegrate paper materials using disintegrator devices equipped with a 3/32 in. (2.4 mm) security screen.
If shredding deviates from the above specification, it must be safeguarded until it reaches the stage where it is rendered unreadable through additional means, such as burning or pulping.
The final shred size requirements must be met prior to release of the shred to an unprotected environment, such as landfill. An agency or, legally authorized agency contractor may shred to a larger size if the paper is protected as it moves through the process until final Safeguards compliant destruction is attained.
Data destruction risks with SSDs
Unlike hard disk drives, SSDs do not use a spinning disk to store data. Instead, they store on flash memory chips. While this leads to both greater durability and data density, it means they’re more difficult to sanitize through traditional methods. In fact, their unique data sanitization requirements can cause data security issues when it comes time for data erasure or destruction.
Types of data destruction and how they affect SSD erasure
- Degaussing, a tried and true data destruction technique that rearranges the magnetic fields on electronic media, is not effective on most flash-based memory devices, including SSDs. This is because SSDs use integrated circuit (IC) assemblies (interconnected flash memory chips) to store data instead of storing it magnetically. So, if care is not taken to separate SSDs from HDDs during degaussing, the data stored on SSDs will be left behind.
- Cryptographic erasure, is a newer form of data sanitization. Technically speaking, however, it does not destroy the data itself. Instead, it is a highly efficient way of sanitizing disks that have encrypted data. It deletes all of a drive’s encryption security keys and replaces them with new ones, effectively obscuring the data that remains. However, users can impact the quality of encryption and the resulting success of cryptographic erasure during key generation. Also, if sensitive data is saved to the disk before encryption occurs, the unencrypted data will still be recoverable. The use of Cryptographic Erase is inconsistent from SSD manufacturer to manufacturer, too, which further complicates the process. This further introduces risk when using cryptographic erasure as a primary data sanitization method.
- Physical destruction such as shredding or crushing is the ideal form of data destruction for many storage mediums; however, SSDs are not fully destroyed by standard hard disk drive shredders. The common shred sizes of these machines fail to fully destroy the data chips on high-density SSDs, which can require shred sizes as small as 2 millimeters (per the U.S.’s National Security Agency (NSA)). And, with data storage density continually increasing, the result of shredding at larger sizes is that SSD IC chips can remain fully intact, and information can still be recoverable by hackers.
- File shredding or wiping destroys data on individual files and folders by data overwriting, but typically doesn’t reach the hidden or overprovisioning areas of an SSD. For SSDs, overprovisioning is the practice of including extra storage capacity on a disk to spread out read/write wear across a larger data storage area. Even with this tactic, repeated binary overwriting shortens the lifespans of SSDs by increasing wear overall. Also, unless you can independently confirm that data has been deleted, most “pre-installed” data wiping utilities aren’t secure or reliable. This is important because of technical hindrances to overwriting, such as the presence of BIOS freeze locks. Freeze locks can prevent some low-level, firmware-based erasure commands from being executed successfully, causing the erasure to fail.
Common Practices that do not Permanently Delete Files
Deleting:
Existing Windows commands related to data deletion, like Delete, Empty Recycle Bin, Clear History, and Delete Temporary Internet Files in Microsoft Internet Explorer do not completely erase information from the disk drive; they only delete file header information. It is possible to recover deleted files from a computer using low-level disk editors, or using one of several data recovery software applications.
Repartitioning:
Repartitioning is the process of changing the size and sequence of partitions on a disk to prepare the drive for formatting.
A common misconception is that repartitioning a disk will erase all deleted files stored on a hard drive. Repartitioning the drive only alters the partition tables stored on the disk. Further, deleting a partition only erases the few bytes of data that define the partition, leaving all file data on the hard drive intact.
There are several programs available that can restore a disk’s integrity after a partition has been erased. Repartitioning a drive makes it extremely easy to recover an entire hard drive, including previously deleted files.
Formatting:
Formatting a drive has two purposes. First, it recreates the master file tables that keep track of where file contents are stored on the disk. And second, it verifies each sector is okay to read and write to.
Even though performing a low-level format is time-consuming, it does not actually erase the contents of files organized by the master file tables. After a format, all contents of the deleted files can be resurrected from their deleted state with minimal effort.
Deleting and Defragmenting:
When a file is deleted, the clusters or location on the disk are marked in the Master File Table as being free. The total number of free clusters on a disk constitutes the free space of that disk. The contents of deleted files reside in the free space until they are replaced with new files. If unreplaced, deleted files remain intact. Defragmenting the drive consolidates unused clusters, but does not overwrite the information.
Document Migration:
Many operations performed by the operating system and application programs store data in “hidden” files. Both the operating system and the application programs used on a daily basis create temporary files that contain data for purposes of protecting users from data loss resulting from improper shutdown of application. This phenomenon has been termed document migration.
To observe how document migration occurs, first, turn on the ability to see hidden system files in Windows by going to your computer’s file explorer and selecting file options. Next, create a Word document in an empty folder and browse the document folder while editing the document. Notice that there are now many additional files residing in the same folder as your newly created document. These hidden files contain all details of your document’s information. When the document is closed the application simply deletes these files using standard Microsoft delete functions which makes these files easy to undelete. The Word document has spread its contents to other areas of the disk without your knowledge.