In order to respond to Emergency Directive 21-04, the GPO DI-BWTST Windows – Point and Print Restrictions Disabled was removed from the environment and replaced with the following GPOs: DI – USGS Windows Restrict Driver Installation to Admins and DI – BWTST Point and Print Restrictions Enforced v2. The first GPO configured the setting RestrictDriverInstallationToAdministrators to prevent non-administrators from installing printer drivers on a print server. The GPO is Security Filtered on the AD Group IGSGBWTST Computers – Print Servers. The AD group and was pre-populated with a known list of computers (servers and clients) that had previously shared/published printers to Enterprise Active Directory.
The second GPO enforced the new recommended Point and Print configurations as described in KB5005010: Restricting installation of new printer drivers after applying the July 6, 2021 updates. To ensure that these settings were rapidly deployed, the BigFix fixlet GS-Policy: Enforce Windows Point and Print Restriction Settings – Emergency Directive 21-04 was deployed to all Windows endpoints.
An alternative remediation option for servers that do not function as print servers was to shut down and disable the Print Spooler Service. The BigFix fixlet DOI: Spooler Services Control was offered for use by local sites that wish to disable the Print Spooler Service. Reminder that taking this action will prevent local and remote printing.
These new Point and Print settings have caused some issues with the printer driver mapping process when shared from a Windows Print Server. After configuring the RestrictDriverInstallationToAdministrators setting to 1, users must provide an administrator username and password when prompted for credentials when attempting to install a print driver. This will occur the first time a local print mapping logon script/GPO is run or when a system has an older print driver than what is hosted on the Print Server.
Best Practices when dealing with Print Driver installs prompting for Admin
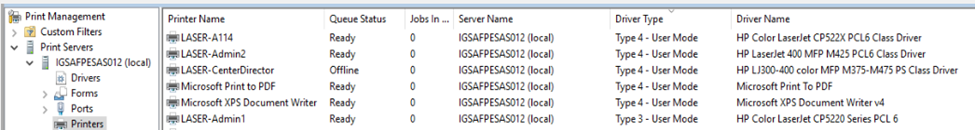
- Use Type 4 Drivers when Available. When installing Print Drivers via GPO, the driver must be signed by a trusted digital signature and the driver must be packed (Package-aware print drivers). Installing of the unpacked (non-package-aware) drivers through Point and Print Restrictions is impossible. You can check your Driver Type on the print server under the node Print Management > Print Servers > Server Name > Printers.
Microsoft recommends using Group Policy to install printers on users’ computers but this only works seamlessly for v4 Package-aware print drivers. When installing any v3 driver, a UAC window appears asking for an administrator password.
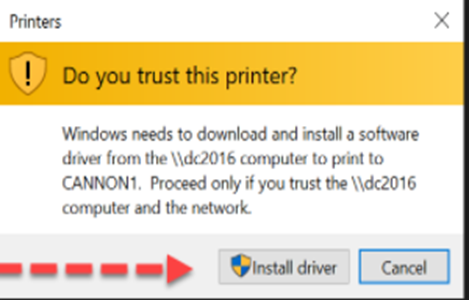
v4 Package-aware print drivers will not prompt for admin when installed via GPO.
Under Advanced in the installed printer properties on the print server, click “New Driver”
Select make/model. It’s not always obvious which driver type you’ve downloaded so click “Next” and it will show you if it’s a Type 3 or Type 4 driver as shown below. If your model isn’t listed, you can try Windows Update.
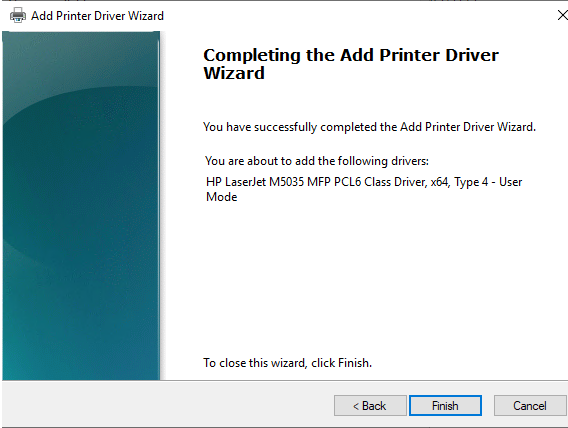
If your printer doesn’t have a Type 4 driver through Windows, you will need to search the manufacturer’s support website for v4 drivers and install them when available.
2. If you cannot use v4 drivers for your printers or they do not exist for your printer model, use a GPO to install print drivers at logon for new users and be available during their first logon to assist with admin rights. The UAC prompt will come up for each different type of v3 driver. Use Global or Universal print drivers when available to limit the amount of print drivers that are needed to be installed.
3. Some sites have moved from using Windows Server Print Management to a software service for Print Management like PrinterLogic. The TSTs are looking into a demo of this for pricing and consideration.