Background
On July 29, 2020, Microsoft published security advisory 200011 that describes a new vulnerability that’s related to Secure Boot. Devices that trust the Microsoft third-party Unified Extensible Firmware Interface (UEFI) Certificate Authority (CA) in their Secure Boot configuration may be susceptible to an attacker who has administrative privileges or physical access to the device.
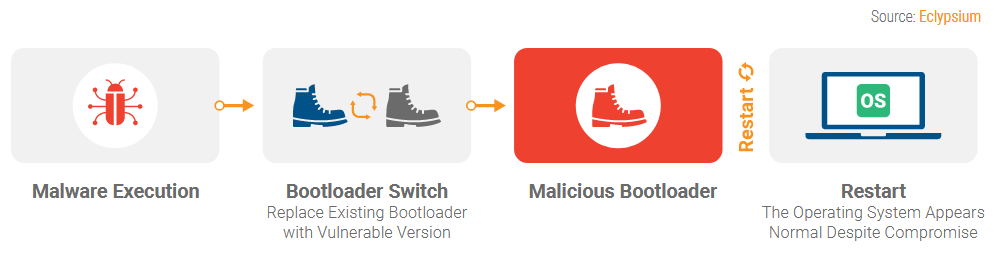
Researchers say BootHole allows attackers to tamper with the GRUB2 component to insert and execute malicious code during the boot-loading process, effectively allowing attackers to plant code that has full control of the OS, launched at a later point.
This type of malware is usually known as a bootkit because it lives inside bootloaders, in the motherboard physical memory, in locations separate from the actual OS, allowing it to survive OS reinstalls.
Below is an illustration of a rootkit attack
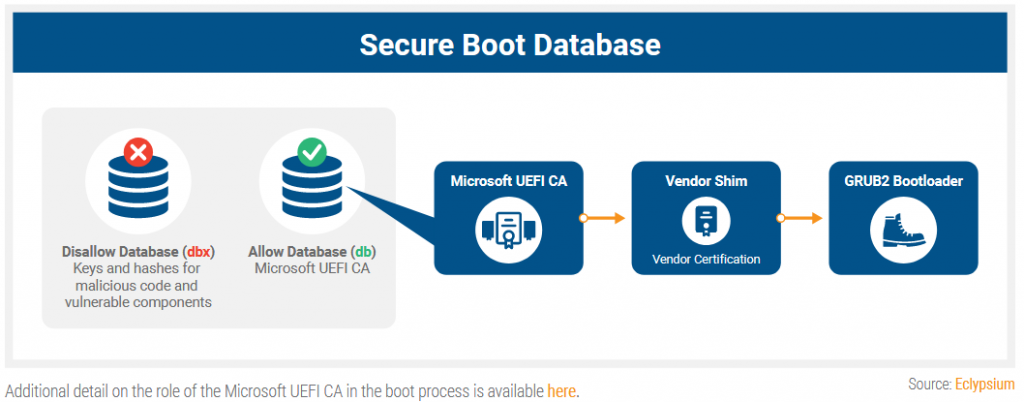
Typically the UEFI secure boot process will use a series of certificates to either allow or disallow certain boot processes
Identifying systems at risk
Tenable has the following plugin that reports vulnerable systems Windows Security Feature Bypass in Secure Boot (BootHole) | Tenable®
Systems that are vulnerable will be set for UEFI and have secure Boot enabled
Resolution
Step 1
Verify that either
or
are installed
Step 2
You should follow these steps only if the following conditions are true:
- You have verified that your device trusts the third-party UEFI CA in your Secure Boot configuration. To do this, run the following line of PowerShell from an administrative PowerShell session:
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI db).bytes) -match 'Microsoft Corporation UEFI CA 2011' - You do not rely on starting any of the boot applications that are being blocked by this update. (this should not apply to any systems in USGS)
Step 3
After you read the warnings and verify that your device is compatible, follow these steps to update the Secure Boot DBX:
- Download the appropriate UEFI Revocation List File (Dbxupdate.bin) for your platform (x86,x64,ARM) from https://uefi.org/revocationlistfile.
- You will have to split the Dbxupdate_x##.bin file into the necessary components in order to apply them by using PowerShell cmdlets. To do this, follow these steps
- Download the PowerShell script from PowerShell Gallery | SplitDbxContent.ps1 1.0
- Run the downloaded PowerShell script on the Dbxupdate_x##.bin file: (Note: cd to directory)
- For 64Bit
./SplitDbxContent.ps1 “c:\path\to\file\dbxupdate_x64.bin”
- For 32Bit
- ./
SplitDbxContent.ps1 “c:\path\to\file\dbxupdate_x86.bin”
- ./
- Verify that the command created the following files:
- Content.bin – update contents
- Signature.p7 – signature authorizing the update process
- For 64Bit
- In an administrative PowerShell session, run the Set-SecureBootUefi cmdlet to apply the DBX update:
Set-SecureBootUefi -Name dbx -ContentFilePath .\content.bin -SignedFilePath .\signature.p7 -Time 2010-03-06T19:17:21Z -AppendWrite
- Restart the device to complete the process
You can visit Microsoft guidance for applying Secure Boot DBX update for more information