This article addresses some common issues during the BitLocker encryption process and provides guidance to troubleshoot these issues.
NOTE: The MBAM Client does not start BitLocker Drive Encryption actions if a remote desktop protocol connection is active. All remote console connections must be closed and a user must be logged on to a console session before BitLocker Drive Encryption begins. If the McAfee software does not fully uninstall try the following steps in order. Trusted Platform Module (TPM) technology is designed to provide hardware-based, security-related functions. A TPM chip is a secure crypto-processor that helps you with actions such as generating, storing, and limiting the use of cryptographic keys. BIOS may require an update to resolve repeated TPM errors, check with hardware vendor to see if an update is available. WARNING: To avoid having to preform BitLocker recovery when updating the BIOS BitLocker must be suspended one of the following actions: To determine whether a TPM chip complies with latest Windows standards, From PowerShell as Admin, enter cmdlet: If output is equal to If attempts to Clear TPM fails to reset the TPM, launch a PowerShell as Admin, enter cmdlet: If event Viewer logs are saying anything about TPM errors OR Click Security processor troubleshooting. If TPM management console fails to load and BitLocker status is suspended. If ‘Clear TPM‘ action does not resolve the issue. Please attempt to following actions: It is highly recommended the manual reverification of the system’s Key Escrow. Do not assume that the system’s Recovery Key is functioning properly after a TPM failure. Microsoft BitLocker Administration and Monitoring (MBAM) provides a simplified administrative interface that you can use to manage BitLocker Drive Encryption. Please review MBAM logs in Event Viewer for possible causes of issues such as TPM not being active, not able to communicate with server etc. PATH: Event Viewer/Application and Services logs/Microsoft/Windows/MBAM/ MBAMClientUI.exe is Microsoft BitLocker Administration and Monitoring (MBAM) Client software. Or Run As Admin: PowerShell cmdlt. If the encryption status does not pop up. You can manually launch the notification utility by searching for In some cases, even after manually running MBAMClientUI.exe a stalled systems would still not encrypt. This could be because but not limited to old hardware, MBR to GPT conversion failure, operating system (OS) upgraded, Windows Recovery Environment (WinRE) corrupted, or general unknown reasons. The following instructions are to have you perform a Startup Repair on the effected system. Example Error: BitLocker could not be enable. If a ‘manage-bde’ command returns back as Invalid Namespace error. Run as Admin a cmd prompt the following command. Next re-run the ‘manage-bde’ command. A Self-Encrypting Disk (SED) Solid State Drives (SSD) may try to encrypt using the hardware encryption but this maybe vulnerable to attack, BitLocker should be used to enforce software encryption. This can be verified by doing the following: Please utilize the BigFix Web Report: GS: Windows Workstations – BitLocker Status to verify that both GPOs “DI – USGS Windows Client FIPS Enabled” and “ITSOT – BitLocker Settings” have been applied to the targeted system. If you find systems that are not applying the GPOs correctly despite having successfully running the cmdlet: McAfee Troubleshooting
McAfee Software did not fully uninstalled
Trusted Platform Module (TPM) Troubleshooting
Bios Update
Suspend-BitLocker -Mountpoint "C:"TpmReady: False
Get-TPM output should be similar too TpmReady: True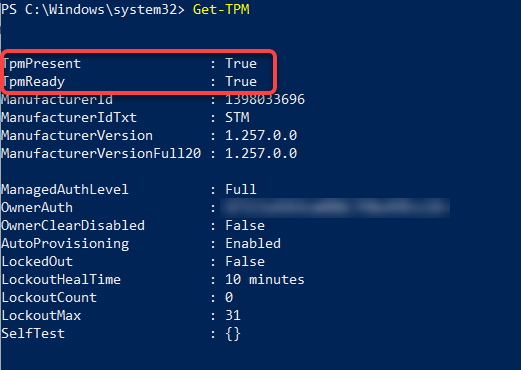
TpmReady: False, please attempt to reset the TPM via Clear TPM actions. 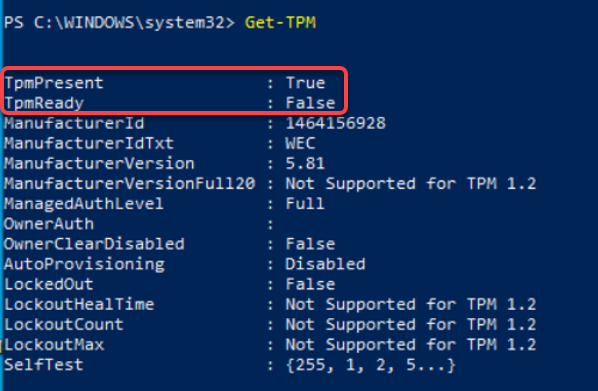
Initialize-Tpm -AllowClear -AllowPhysicalPresence the return output should be similar to 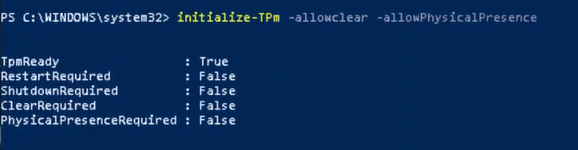
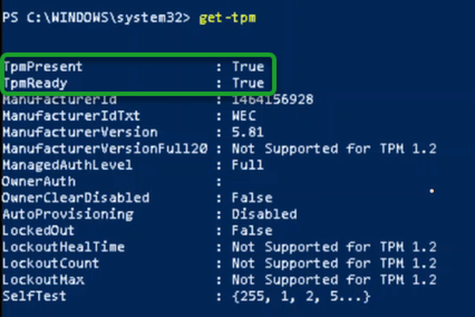
TPM Not enabled in BIOS
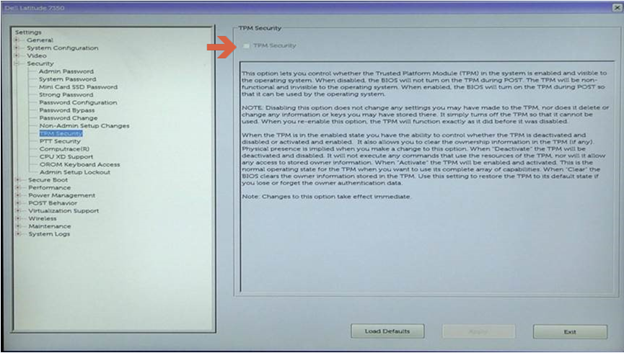
Clear TPM
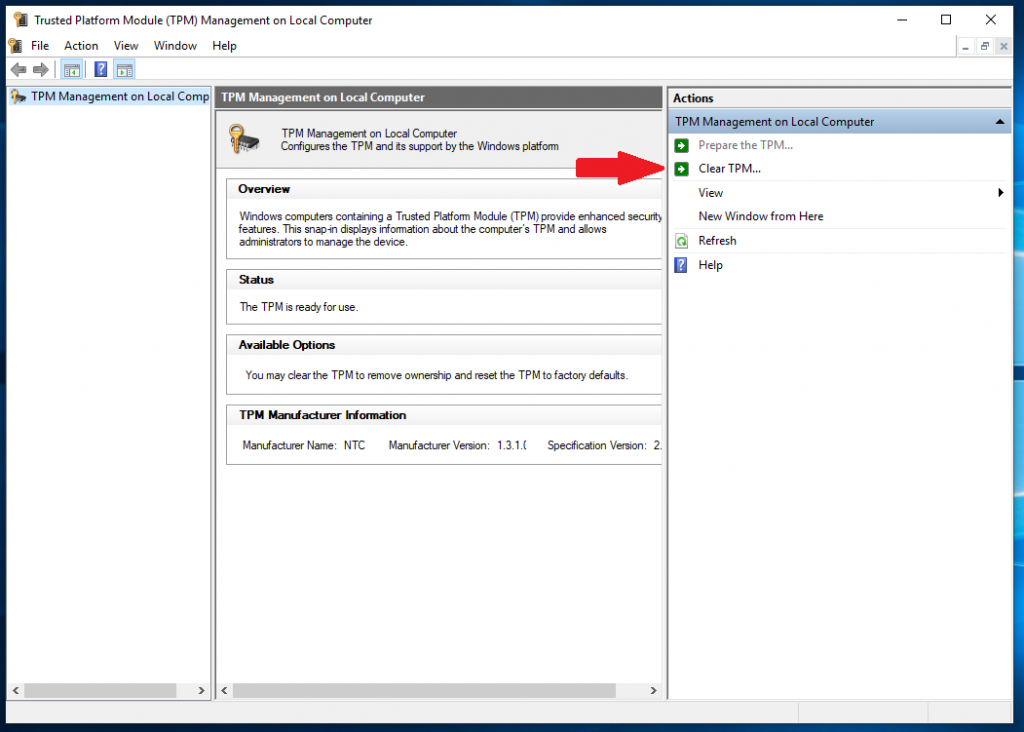
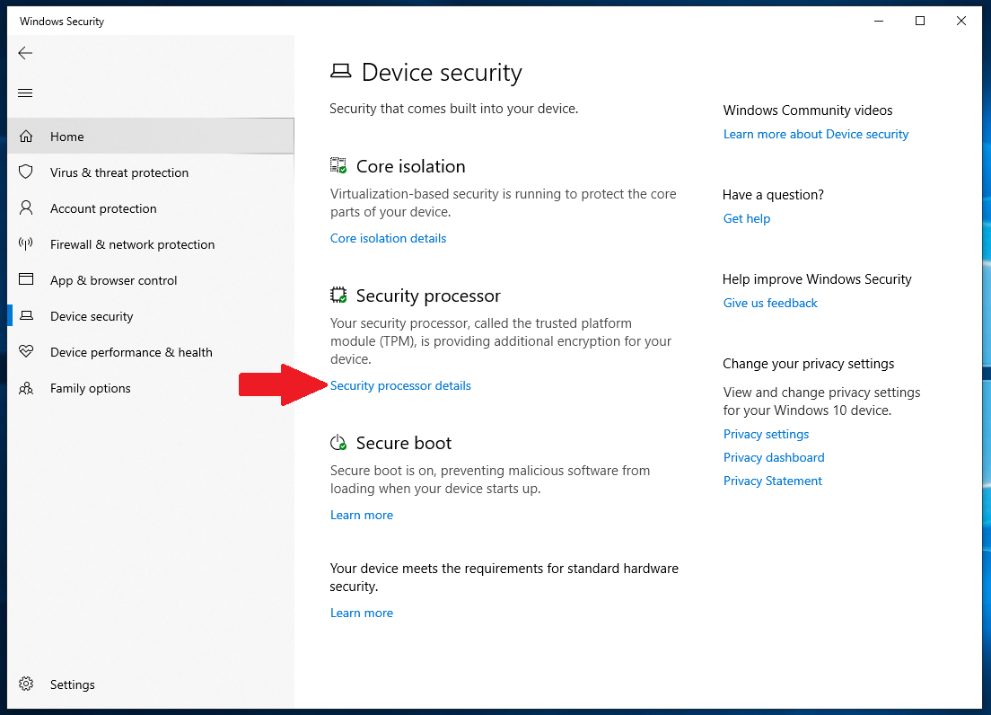
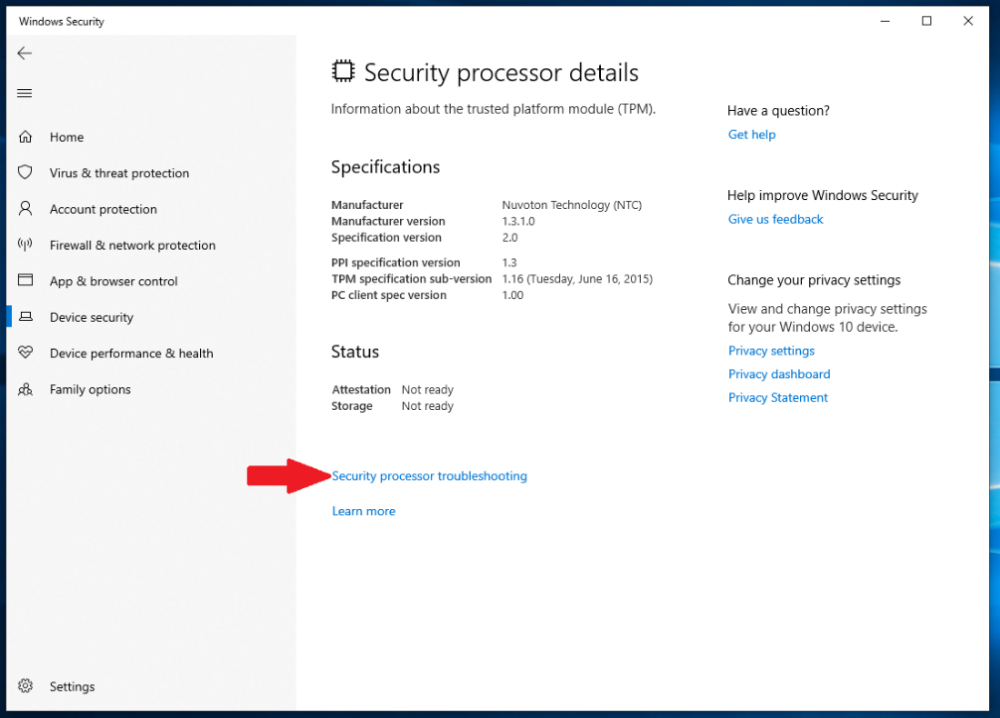
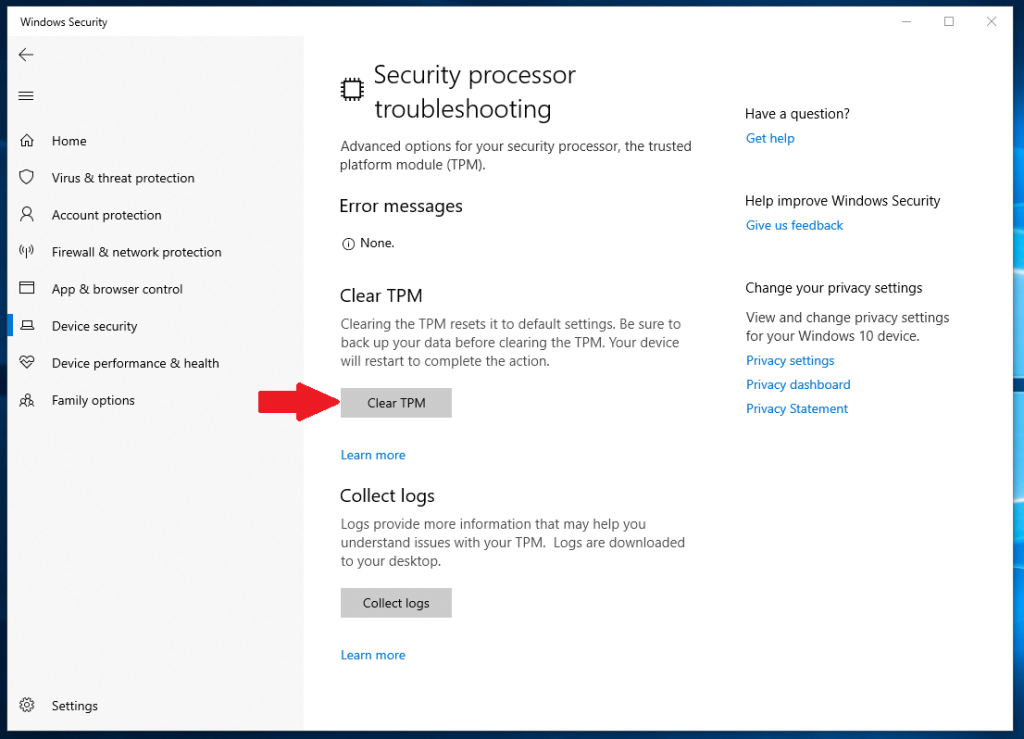
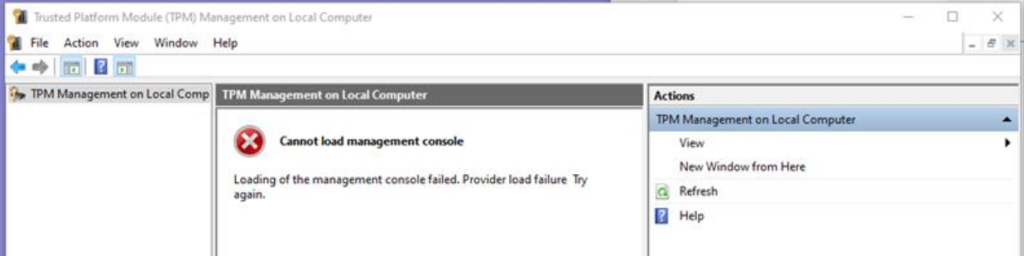
TPM Management Console fails to load causing BitLocker Suspended
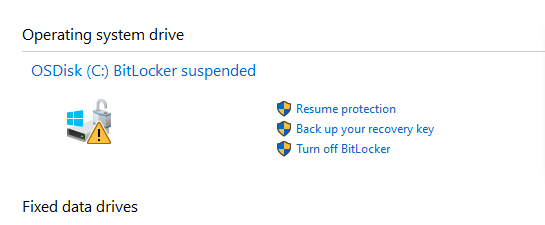
Microsoft BitLocker Administration and Monitoring (MBAM) Troubleshooting
MBAM Logs
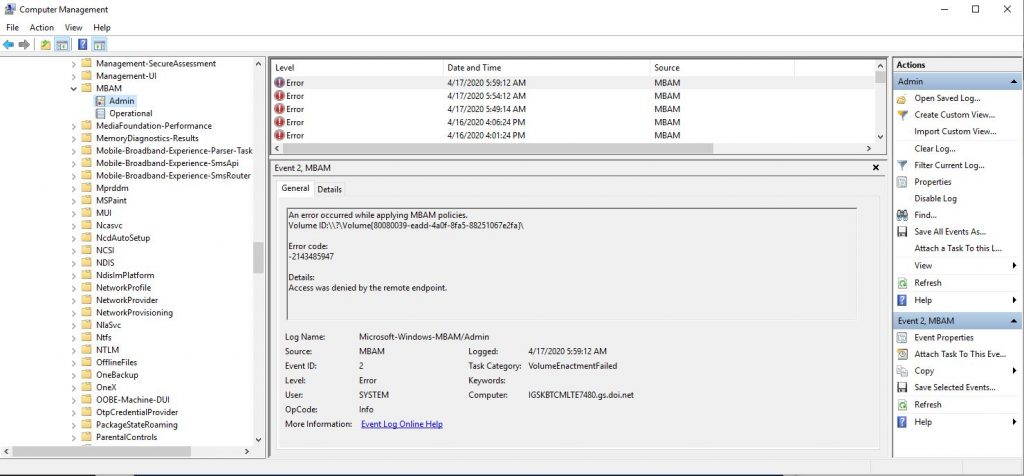
MBAM Stalling
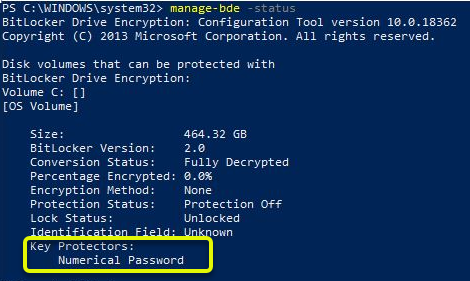
manage-bde -status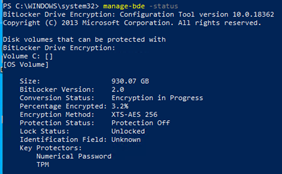
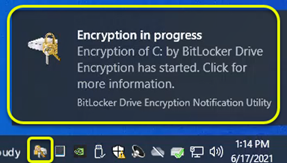
BitLocker Drive Encryption Notification Utility
fvenotify.exe
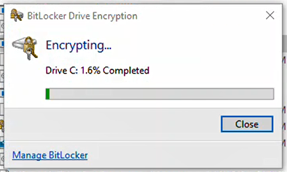
Pop-Up - BitLocker could not be enable
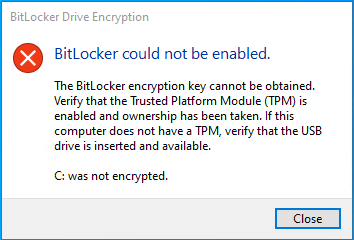
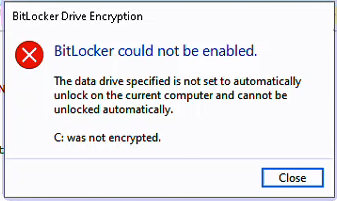
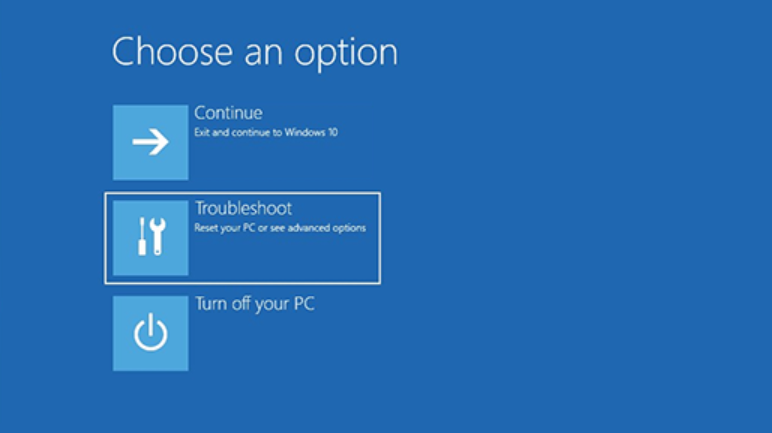
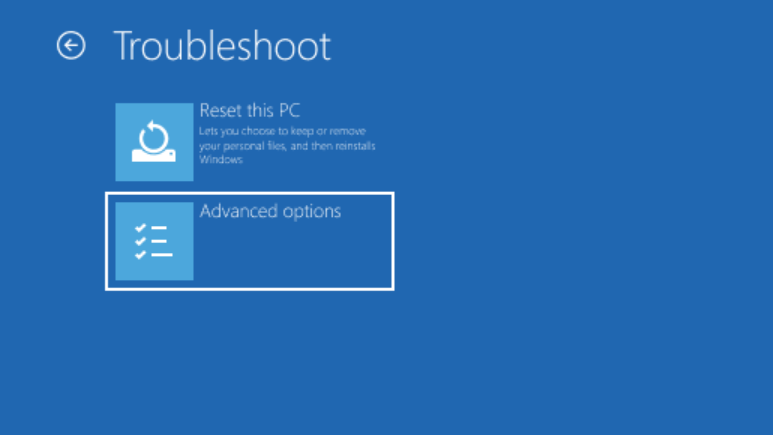
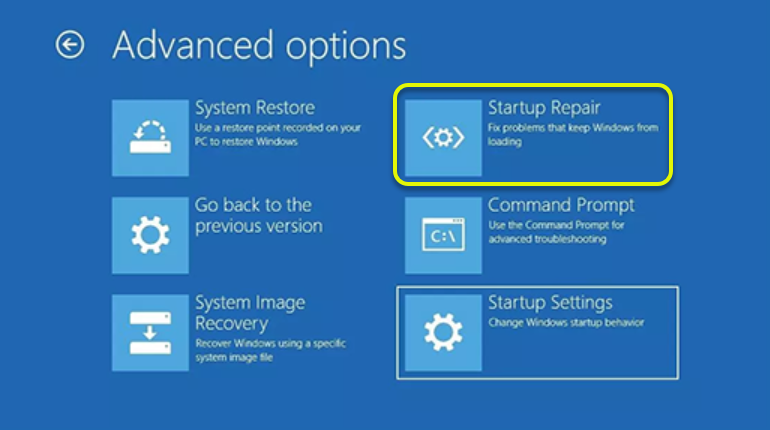
manage-bde -status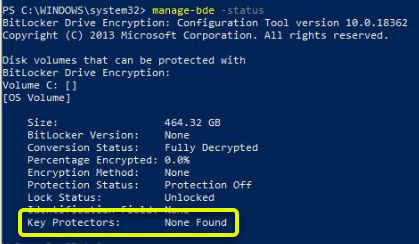
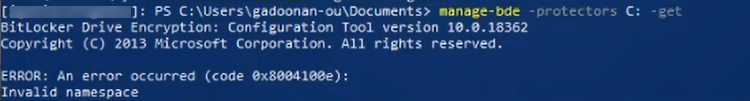
Invalid NameSpace Error
mofcomp.exe c:\windows\system32\wbem\win32_encryptablevolume.mof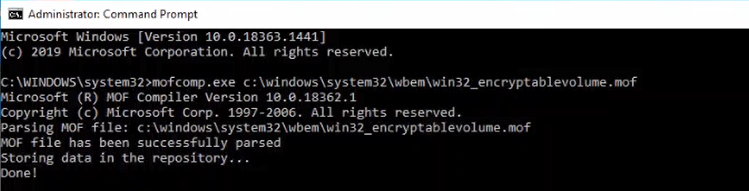
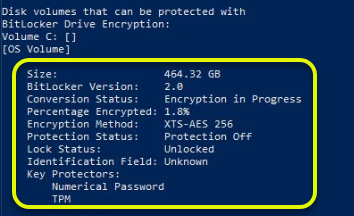
manage-bde -status
Self-Encrypting Disk (SED) Solid State Drives (SSD)
AD/MECM Policy Troubleshooting
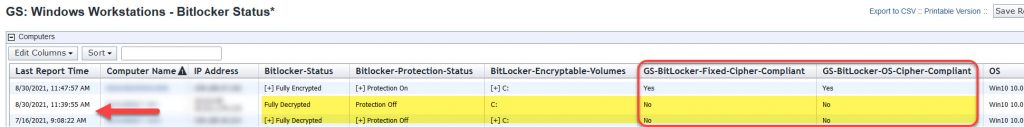
gpupdate /force , please reference the TST page: “Fixing Group Policy Update Failures Due to LocalGPO Processing Errors” to attempt at resolving the issue.