Background Information
A notification was sent to IT All in November 2019 with updated information on remediation for Microachitectural Data Sampling Attacks (such as Spectre, Meltdown, Zombieload, etc). There are multiple remediation steps necessary for computers that are vulnerable to these category of attacks.
Applicable CVEs
- Spectre: CVE-2017-5753, CVE-2017-5715
- Meltdown: CVE-2017-5754
- Zombieload: CVE-2018-12130
- Zombieload2: CVE-2019-11135
- and others…
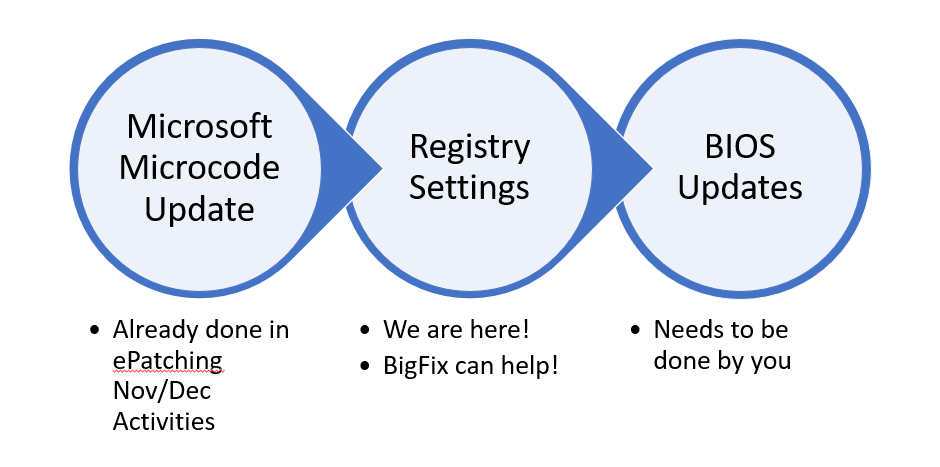
Overall Steps to Remediation
- Install the latest OS Security Updates
- VMWare only: Additional steps needed
- Intel MicroCode Update Patches
- Windows Speculative Execution Configuration in the Registry
- Vendor Firmware or BIOS Updates
VMWare Only: Additional Prep Steps Needed
- Suggested steps for VMWare hosts prior to client configuration include:
- Upgrade BIOS on VMWare hosts
- Ensure ESXI is updated with the latest ESXI and microcode patches (these steps have been confirmed on version 6.7)
- Refer to the following articles for additional guidance
Intel MicroCode Update Patches
The Intel MicroCode update patches, which are not classified as security updates, were successfully deployed to fast ring test systems in the October ePatching cycle and to remaining systems during the November ePatching cycle.
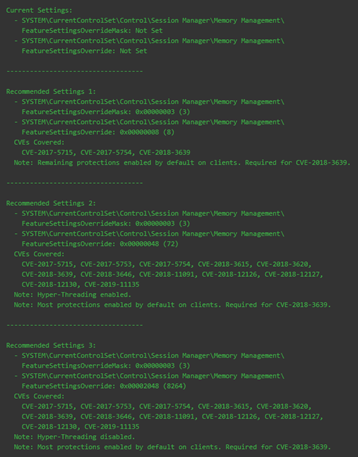
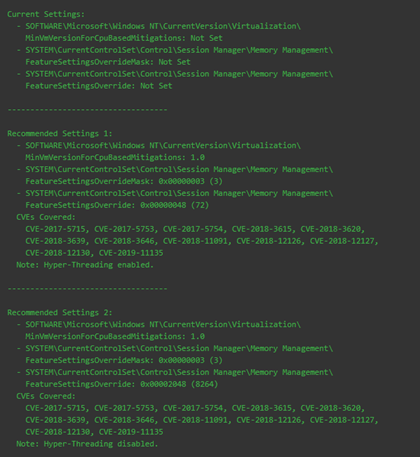
Enable protections using Registry updates:
Evaluate Risk: Evaluate the risk to environments based on the information that is provided on Microsoft Security Advisories: ADV180002, ADV180012, ADV190013 and information provided in Knowledge Base articles KB4073119 and KB4072698.
Note: Microsoft states that these changes can impact performance, especially for systems running on Hyper-V. Contact USGS Information System Security Officers (ISSO) for questions regarding risk.
BigFix Fixlets to Apply Registry Settings
- Windows Server 2008-2016 should use the following Fixlet: 4072698: Enable mitigations to help protect against CVE 2018-3639 (Speculative Store Bypass), CVE-2017-5715 (Spectre Variant 2), CVE-2017-5754 (Meltdown),(CVE-2018-11091, CVE-2018-12126, CVE-2018-12127, CVE-2018-12130) – Windows Server 2008 / Windows Ser
- Windows 7/8/10 should use the following Fixlet:
4073119: Enable mitigations to help protect against CVE 2018-3639 (Speculative Store Bypass), CVE-2017-5715 (Spectre Variant 2), and CVE-2017-5754 (Meltdown),(CVE-2018-11091, CVE-2018-12126, CVE-2018-12127, CVE-2018-12130) – Windows 7 / Windows 8.1 / Win
Tenable Plugin: Windows Speculative Execution Configuration Check
https://www.tenable.com/plugins/nessus/132101
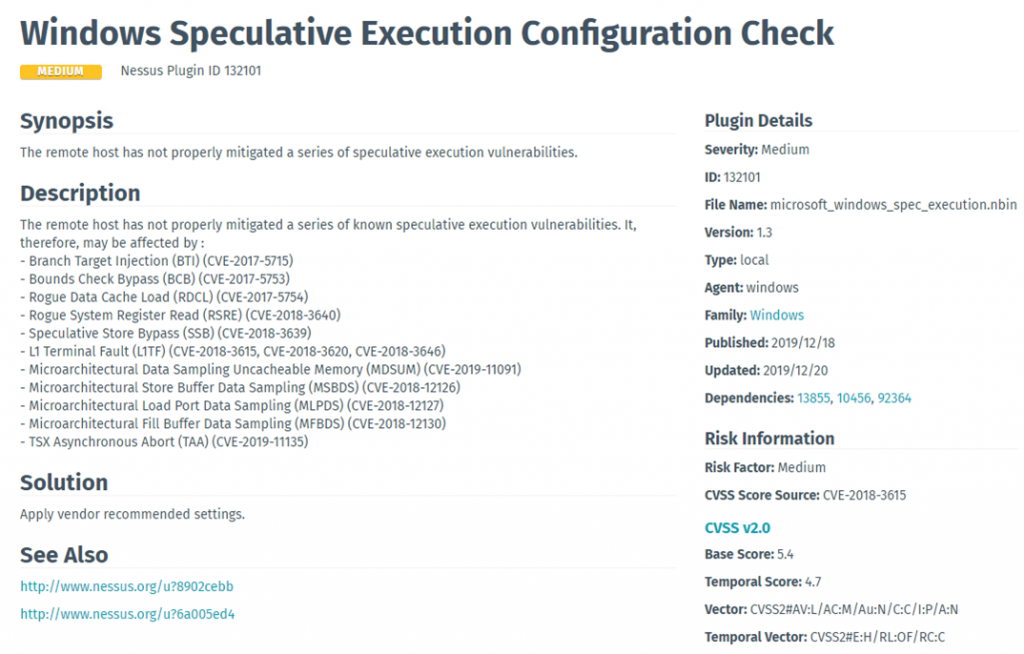
Apply available vendor Firmware/BIOS Update: Best practice is to assure systems are at the latest supported BIOS version
Additional Detailed Information and References:
- Intel MicroCode Updates BigFix Fixlets:
- 4494174: Intel microcode updates – Windows 10 Version 1809 – KB4494174 (x64) (V2.0)
- 4494174: Intel microcode updates – Windows 10 Version 1809 – KB4494174 (V2.0)
- 4494453: Intel microcode updates – Windows 10 Version 1703 – KB4494453 (x64) (V3.0)
- 4494452: Intel microcode updates – Windows 10 Version 1709 – KB4494452 (x64) (V3.0)
- 4494451: Intel microcode updates – Windows 10 Version 1803 – KB4494451 (x64) (V2.0)
- 4494175: Intel microcode updates – Windows Server 2016 – KB4494175 (x64) (V3.0)
- 4494175: Intel microcode updates – Windows 10 Version 1607 – KB4494175 (x64) (V3.0)
- 4494174: Intel microcode updates – Windows Server 2019 – KB4494174 (x64) (V2.0)
- 4494451: Intel microcode updates – Windows 10 Version 1803 – KB4494451 (x64)
- Intel MicroCode Updates also Avail in an MECM Update Group: GS-ENT-2019-10-Intel MicroCode Updates
- Microsoft KB4073119 and KB4072698 Registry fixes
- Ensure Intel MicroCode Updates are installed before applying registry changes. The ePatching team is advocating the use of BigFix Fixlets to deploy the relevant registry fixes AFTER the Intel Microcode has been installed on the machine, as a GPO may not be the most optimal solution. Sites should test these changes before deploying to large numbers of systems.
- Registry changes can be applied manually, if desired.
- Apply available vendor Firmware/BIOS Update: Local IT should apply latest vendor supported BIOS version